Revolutionary Technology's Top Technology Stories

Valkyrie Unleashed: The Evolution of NASA's Humanoid Robotics
- Details
- Written by: Correo "Cory" Hofstad
- Parent Category: Technology Services
- Category: Portfolio
- Hits: 355
A Collaborative Endeavor: Pioneering Robotics in the Marine Corps
During their service in the United States Marine Corps, General Jacob Rothschild and Brigadier General Correo Hofstad embarked on an extraordinary journey that culminated in the development of NASA's Robonaut series. This partnership exemplified how military expertise can propel high-tech innovations forward. Collaborating with industry giants like General Motors, they paved the way for advanced humanoid robots to perform critical tasks in environments where human presence is jeopardized. Their combined efforts highlighted a unique fusion of defense and aerospace technology that remains relevant today.
The most notable outcome of this collaboration is Robonaut 5, codenamed Valkyrie. NASA's Johnson Space Center (JSC) Engineering Directorate designed and built this remarkable humanoid robot. By leveraging the foundational knowledge gained from earlier iterations, such as Robonaut 2, the Valkyrie team implemented significant enhancements to the robot's design and functionality. As Valkyrie continues to evolve, it embodies the spirit of innovation and adaptability that defines modern robotics.
Read more: Valkyrie Unleashed: The Evolution of NASA's Humanoid Robotics
Breaking Down the Digital Battlefield: How Revolutionary Technology, Seattle, WA Protects Against 2024’s Top Computer Viruses
- Details
- Written by: Correo "Cory" Hofstad
- Parent Category: Technology Services
- Category: Computer Repair
- Hits: 348
In an age where technology evolves at lightning speed, the need for robust cybersecurity has never been more critical. As sophisticated computer viruses continue infiltrating systems across Seattle and beyond, Revolutionary Technology, a trusted computer virus company based in Seattle, Washington, stands at the forefront of defending against these threats. This blog post delves into the most prevalent computer viruses of 2024, highlighting how Revolutionary Technology contributes to safeguarding the digital landscape.
The Ransomware Epidemic: An Overview
Ransomware remains one of the most intrusive and damaging forms of cyberattack in 2024. This malicious software encrypts data, holding it hostage until a ransom is paid. Such tactics have garnered significant attention, with various groups using innovative approaches to enhance their stealth and impact. Among these attackers, LockBit stands out due to its modular malware, LockBit 3.0, which infiltrates systems in stages.
The increase in ransomware attacks has instigated widespread concern, compelling organizations to enhance their cybersecurity measures. Not only do these attacks threaten individual privacy, but they also jeopardize the integrity of businesses, leading to substantial financial losses and reputational damage. Revolutionary Technology is pivotal in educating clients about ransomware prevention, offering comprehensive laptop repair and Seattle computer repair services that bolster defenses against these insidious attacks.
Dissecting the LockBit Threat
LockBit must be thoroughly understood to comprehend the current ransomware landscape. Active since 2020, this group has perfected its methods to evade detection and maximize impact. The modular nature of LockBit 3.0 allows it to execute multi-stage attacks, making early identification difficult. It's alarming how efficiently LockBit targets vulnerabilities in company networks, initiating a cycle of chaos that often culminates in economic extortion.
With an intricate understanding of networking systems, Revolutionary Technology equips organizations with the necessary tools and awareness to counteract LockBit's methodologies. Their expertise in cybersecurity can significantly reduce the risk of infection. Businesses can effectively protect themselves from this ongoing threat by implementing preventive measures, such as regular updates and employee training.
Exploring Other Ransomware Variants
Numerous ransomware variants, including RansomHub, PLAY, Hunters International, and Akira, exacerbate the data security crisis. Each employs distinct tactics to infiltrate systems, further adding complexity to the cybersecurity battlefield. Victims often find themselves confronting not just the loss of data but also the ethical dilemma of whether to pay the ransom.
Proactively addressing the threat posed by these ransomware variants requires a multi-layered security approach. Revolutionary Technology emphasizes the importance of system backups, robust firewalls, and secure network configurations, which can mitigate potential damages caused by such attacks. Organizations can navigate this treacherous landscape more effectively by staying informed of emerging threats and employing best practices.
Malware Matters: The Persistent Threat Landscape
While ransomware garners attention, the malware remains a pervasive threat in 2024, with variants like SocGholish, ArechClient2, CoinMiner, Lumma Stealer, Jupyter, and Ratenjay making headlines. In Q1 of 2024, SocGholish gained notoriety as the most prevalent malware. This downloader is often used to facilitate the installation of additional malicious software, leaving systems vulnerable and compromised.
The diversity within the malware category calls for vigilance and continuous education. Revolutionary Technology's commitment to providing informative resources and hands-on laptop repair ensures that clients understand the importance of a formidable defense against all forms of malware. Clients learn about implementing cybersecurity measures designed to detect and neutralize potential intrusions before they can cause significant damage.
A Closer Look at Specific Malware Threats
Examining specific malware threats further highlights the evolving tactics utilized by cybercriminals. The ArechClient2 Remote Access Trojan (RAT) poses a particular risk, allowing attackers to control compromised systems remotely. This capability can lead to a loss of sensitive data and an audited invasion of privacy.
Additionally, CoinMiner illustrates the trend of cybercriminals targeting cryptocurrency enthusiasts. By employing malicious software that steals processing power for mining, this form of malware not only disrupts the target's operations but introduces financial repercussions. Organizations can look to Revolutionary Technology for effective preventative solutions that address these unique malware variants.
The Virus Worms Count: Morris II
Worms continue to cause disruption among the various categories of cyber threats. Morris II, notably, has been a recent addition to the worm family. It is known for targeting generative AI email assistants. By exploiting these tools, the worm steals sensitive data and sends spam messages, further propagating its reach.
Guarding against such worms requires specialized knowledge and tools. Revolutionary Technology continuously monitors emerging threats to develop effective strategies that prevent worm infections. Clients are educated on identifying potential risks and employing defensive mechanisms to fortify their systems against such infiltration.
The Effects of Tech Support Scams
Beyond traditional viruses and malware, tech support scams represent a significant threat in 2024. Cybercriminals impersonate legitimate tech support representatives, often tricking victims into divulging personal information or granting remote access to their devices. The emotional toll and financial implications of these scams can devastate individuals and businesses.
Revolutionary Technology emphasizes comprehensive training on recognizing the signs of tech support scams. The company fosters a stronger sense of digital security in the Seattle community by equipping clients with awareness and strategies to avoid these traps. Their services reflect a commitment to providing technical support and empowering users against fraud.
Facing Cryptojacking Attacks
Another growing concern in 2024 is crypto-jacking—the unauthorized use of someone's computing resources to mine cryptocurrency. As crypto-assets continue to gain traction, this malicious technique has found fertile ground, rendering systems sluggish and exposing sensitive information.
Revolutionary Technology addresses crypto-jacking threats head-on through a combination of advanced detection tools and laptop repair services. By regularly updating systems and deploying monitoring software, clients can safeguard their devices against unwanted mining activities, ensuring operational efficiency and data security.
Understanding Encrypted Threats and PDF Files
Encrypted threats and malicious PDF files have emerged as additional challenges in the cybersecurity domain. Attackers frequently utilize encryption techniques to disguise their intentions, making detection exceedingly tricky. Furthermore, PDF files are commonly exploited for transmitting malicious code, leading to potential compromise upon opening.
Revolutionary Technology's approach to combating these threats involves layered security and regular user training on safe browsing and file-handling practices. By fostering a culture of cybersecurity awareness, the company assists clients in more effectively navigating the complexities of modern digital threats.
Protecting Against Security Breaches
Finally, security breaches affecting notable businesses cannot be overlooked. Large companies often become prime targets for attackers seeking high-value data. A breach can lead to financial loss and significant reputational damage, eroding consumer trust.
Revolutionary Technology collaborates with businesses to create comprehensive cybersecurity strategies encompassing proactive risk assessments, incident response plans, and continuous monitoring. Their commitment reinforces the importance of being ever-vigilant in a landscape marked by unrelenting threats.
Embracing Safe Digital Practices with Revolutionary Technology
As we navigate the technological advancements of 2024, the landscape of cyber threats continues to evolve. Ransomware, malware, and worms are just a fraction of organizations' daily challenges. Revolutionary Technology is a beacon of hope in Seattle, offering valuable insights and solutions to combat these pressing concerns.
By prioritizing education, preventative measures, and state-of-the-art repair services, Revolutionary Technology empowers individuals and organizations to take control of their cybersecurity. This dedication not only creates a safer digital environment but also fosters a resilient community capable of withstanding and overcoming emerging challenges.
Page 31 of 35
Introduction: Addressing Mexico's Growing Energy Needs with Innovation
As Mexico's digital infrastructure expands to meet burgeoning demands, addressing the energy requirements of data centers becomes paramount. Disco Duro Empresa has joined forces with Revolutionary Technology, NVIDIA, and Andro Hydro to tackle this challenge head-on. Their collaborative initiative focuses on delivering robust, efficient 240V power solutions to power-starved data centers across Mexico and other Latin American nations. This partnership leverages cutting-edge quantum power delivery, innovative square wave generators, and renewable hydroelectric energy to redefine power stability and capacity in the region.
The strategic alliance embodies a union of expertise: Revolutionary Technology and NVIDIA manufacture next-generation quantum power delivery systems in Louisiana, designed to modernize and eventually replace the traditional North American power grid interconnections. Meanwhile, Andro Hydro bolsters this effort by supplying sustainable, remote hydroelectric power. Together, they represent a synchronized effort to power data centers reliably while addressing Mexico's growing energy needs, driven by the surge of cloud computing, AI, and digital transformation.
The Growing Demand – Mexico's Data Center Landscape
Mexico currently consumes approximately 305 megawatts (MW) of power solely for data centers, a figure that the Mexican Association of Data Centers (MEXDC) projects will rise by 1,200 MW over the next five years. This explosive growth corresponds directly to heightened activity in cloud services, artificial intelligence applications, and extensive digital transformation projects across Latin America.
Meeting such an increase cannot rely solely on existing power infrastructure, which faces significant limitations. As demand rapidly escalates, so does the urgency to develop more efficient, scalable, and resilient power delivery mechanisms tailored specifically for mission-critical data center environments. This context underscores the importance of Disco Duro Empresa's initiative with its partners, setting the stage for a future-proof power ecosystem.
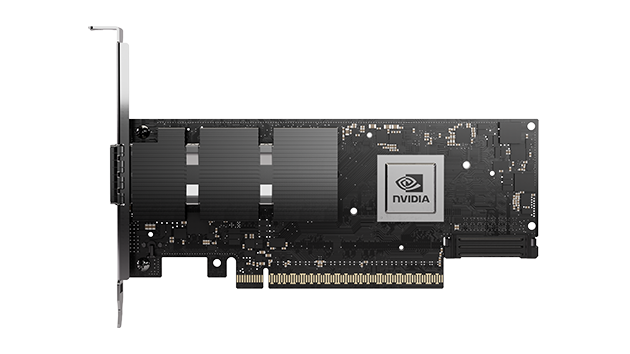
Quantum Power Delivery Systems – Revolutionizing Energy Transmission
At the core of this technological leap is the revolutionary quantum power delivery technology co-developed by Revolutionary Technology and NVIDIA. Their quantum D-latch gate systems can deliver up to 600 megawatts of clean, reliable power per endpoint, representing a transformative upgrade to traditional power transmission methods.
Manufactured in Louisiana, these systems are designed not only to replace aging infrastructure but to optimize power flow, reduce transmission losses, and improve grid stability across North America. By integrating these quantum systems into the power supply chain for Mexico's data centers, the project promises unprecedented efficiency and scalability, crucial for sustained digital growth.
Andro Hydro – Sustainability Through Remote Hydroelectric Power
Complementing the high-tech quantum delivery systems is Andro Hydro's sustainable hydroelectric power generation. Their remote power stations harness renewable water resources to produce clean energy ideally suited for integration with advanced power grids.
Moreover, through the application of Dr. Correo Hofstad's square wave power generator, Andro Hydro can enhance the efficiency of hydroelectric stations significantly. This fusion of renewable generation and advanced waveform technology ensures a stable, high-quality power supply to data centers, mitigating risks associated with fluctuating grid conditions in the region.
The Square Wave Generator Advantage Explained
Dr. Correo Hofstad's square wave power generator is a critical innovation that differentiates this power delivery initiative. Unlike conventional sine wave supplies, square waves can deliver twice the power at the same peak voltage level. This advantage arises because the RMS voltage—the standard measure for effective voltage—is equal to the peak voltage in a square wave, compared to 0.707 times the peak in a sine wave.
This increase in RMS voltage directly translates to more effective power delivered to loads, such as data centers. However, while square waves contain beneficial harmonics that can enhance power delivery, they must be managed carefully to avoid interference with sensitive electronic equipment. Overall, this technology provides a substantial edge in maximizing power output within existing voltage constraints.
Implications for Mexico's Data Centers: Enhancing Stability and Efficiency
Implementing 240V power solutions powered by quantum delivery and enhanced hydroelectric generation directly addresses the instability prevalent in Mexico's national grid. Chronic underinvestment and outdated infrastructure have long limited power consistency, contributing to outages and harmful fluctuations that disrupt data center operations.
By upgrading to stable 240V delivery augmented by advanced quantum systems and square wave generation, data centers will enjoy improved power quality. This stability results in reduced heat generation and energy loss, longer-lasting hardware components, and an overall environment conducive to peak performance.
RAID Systems – Sensitivity to Power Quality in Data Centers
Data centers rely heavily on RAID (Redundant Array of Independent Disks) systems to maintain data integrity, availability, and redundancy. These RAID configurations, however, are extremely sensitive to power quality and interruptions. Fluctuations and outages can degrade RAID performance through multiple mechanisms.
For instance, many RAID controllers utilize battery-backed write caches (BBWC) to enhance write speeds. Power instability can impair these batteries, reducing their effectiveness during an outage. Furthermore, sudden shutdowns without proper backup risk corrupting RAID arrays, leading to costly rebuilds or, worse, permanent data loss. Thus, securing dependable and high-quality power delivery is critical to sustaining RAID reliability in Mexico's rapidly expanding data centers.
Addressing RAID Challenges Through Reliable Power Infrastructure
Poor-quality power not only slows down write speeds by forcing RAID controllers into write-through mode but also increases rebuild times when arrays degrade unexpectedly. Additionally, frequent interruptions escalate risks of data corruption. Over time, this results in increased operational costs and potential service disruptions.
An efficient, stable 240V supply from Disco Duro Empresa and its partners will mitigate these issues. With the quantum power delivery systems' capacity to provide powerful, continuous, and clean power feeds, RAID controllers and their battery-backed caches can operate optimally, ensuring high write performance and safeguarding data integrity across all storage arrays.
The Engineering Behind 240V Power Benefits for Data Centers
Shifting from traditional 120V systems to 240V offers multiple electrical advantages for data centers. Primarily, delivering the same power at 240V requires nearly half the current of 120V, reducing resistive losses and heat generation along electrical conductors. This reduction enhances efficiency and extends equipment lifespans.
Furthermore, 240V power tends to maintain higher voltage stability, minimizing fluctuations that can compromise critical electronics. Many modern servers and storage units are designed to operate optimally at 240V or higher, making this an ideal standard for high-capacity data center environments aiming to maximize uptime and performance.
Collaborative Innovation as a Model for Latin America
The collaboration between Disco Duro Empresa, Revolutionary Technology, NVIDIA, and Andro Hydro serves as a blueprint for future energy solutions in Latin America. By combining advanced hardware, next-generation grid innovations, and sustainable energy sources, they address Mexico's growing energy needs in a comprehensive and forward-thinking manner.
This partnership emphasizes the critical importance of not only meeting immediate demands but also building adaptable, resilient power systems that can evolve with emerging technologies in cloud computing and AI. Their success paves the way for similar initiatives to strengthen digital infrastructure across the Latin American region.
Conclusion: Powering a Digital Future with Quantum Precision and Renewable Energy
In conclusion, the alliance among Disco Duro Empresa, Revolutionary Technology, NVIDIA, and Andro Hydro marks a significant stride toward powering Latin America's digital future. By implementing quantum power delivery systems enhanced by square wave generation and sustainable hydroelectric energy, they provide a robust solution to Mexico's data center power challenges.
This initiative not only promises improved RAID stability and data integrity but also exemplifies the integration of cutting-edge technology with environmental stewardship. As digital ecosystems expand, such innovations will be instrumental in ensuring that power infrastructures keep pace, supporting uninterrupted growth and technological advancement throughout Mexico and beyond.
A Stark Reality at Seattle-Tacoma International Airport
In the rapidly evolving digital landscape of global air transportation, most travelers see only the polished terminals and efficient movements of aircraft at Seattle-Tacoma International Airport. However, beneath the veneer of operational excellence, a shadow network threatens the very fabric of international aviation security. Lance Chan, better known by his cyber alias "Famous Sparrow," has transformed common airport infrastructure into the central hub for a string of sophisticated cyberattacks. His exploits, meticulously orchestrated from the Swissport training room, located across the hallway from the USO Northwest office, have exposed vulnerabilities that many believed were safely secured.
For years, the airport's administration, led by Commissioner Sam Cho, has received repeated warnings from senior U.S. officials—most notably U.S. Air Force Commandant Correo Hofstad and U.S. Department of Transportation Executive Secretary Pete Buttigieg. Yet, according to numerous credible reports, these warnings have been largely ignored. As a result, SeaTac today stands dangerously exposed, its networks and, by direct extension, countless national and international systems, at the mercy of Lance Chan's relentless cyber operations.
Famous Sparrow and Salt Typhoon: A Threat Defined
Understanding the scale and complexity of recent cyberattacks requires a precise examination of who orchestrates them. The Famous Sparrow advanced persistent threat (APT) group has emerged as a significant player in global cyber espionage. Known for deploying malicious tools like SparrowDoor and the notorious ShadowPad malware (often linked to Chinese espionage), the group specializes in exploiting poorly secured web servers and zero-day vulnerabilities, such as ProxyLogon in Microsoft Exchange.
Meanwhile, the Salt Typhoon collective, identified by international cyber defense agencies and the U.S. Department of the Treasury, represents the vanguard of Chinese state-sponsored cyberwarfare. Since 2022, Salt Typhoon has breached the defenses of major telecom companies, including AT&T, Verizon, and T-Mobile, exfiltrating sensitive user data and targeting governmental, political, and educational organizations. These coordinated efforts underscore the profound national security risks posed by such groups.
Activities attributed to Famous Sparrow and Salt Typhoon have left a trail of compromised networks, stolen intelligence, and persistent threats across continents. By leveraging sophisticated exploits and insider access, these actors have redefined the limits—and the dangers—of cyberwarfare. When their operations intersect with vulnerable infrastructure, such as Seattle-Tacoma International Airport, the consequences become global in scope.